In a world where everything is connected online, it is not hard to see why more and more wireless attacks are happening each year. Most of us basically do every single transaction online — from money transfer to shopping goods. We are also transmitting sensitive information every day, and while most people wouldn’t care, it is best to always make sure that your information is in safe hands — no matter what it is. So it’s important that you are aware of these wireless network attacks so you can take necessary actions to counter it.
Types of Wireless Attacks
There are many types of known wireless network attacks — base on their level of security. According to a paper published in Research Gate, these wireless attacks are divided into three criteria: Level I Security, Level II Security, and Level III Security.
- Level I Security – this level of security is based on an algorithm called Wired Equivalent Privacy (WEP). It is designed to overcome most of the security threats by encrypting the data that is being transmitted over the network. Only the recipient with correct WEP address will be able to decrypt the information, it is also used to prevent unauthorized access to wireless networks.
- Level II Security – this is a mid-level security algorithm that addresses most of the security threats that are not resolved by Wired Equivalent Privacy (WEP). Wi-Fi Protected Access (WPA) applies for stronger network access, and supports better security technologies, and enforces data integrity.
- Level III Security – launched in 2004, this is currently the highest level of security available for wireless networks. Also known as 802.1li, this high-level security eliminates most of the security flaws in Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA), providing encryption security of 128-bit for wireless networks. However, just like the lower level securities, it also has its own flaws. It deteriorates in performance every time a user attempts to perform a transaction because the network runs a script to perform security checks and encryption, resulting in slower data transfer rate.
However, we will only tackle the most common wireless attacks. We might also mention which level of security they belong, but you can read in-depth information of these wireless network attacks in the CWNA Official Study Guide 4th Edition, or the paper published in Research Gate titled “Wireless Attacks” which we have mentioned above.
1. Rogue Wireless Device
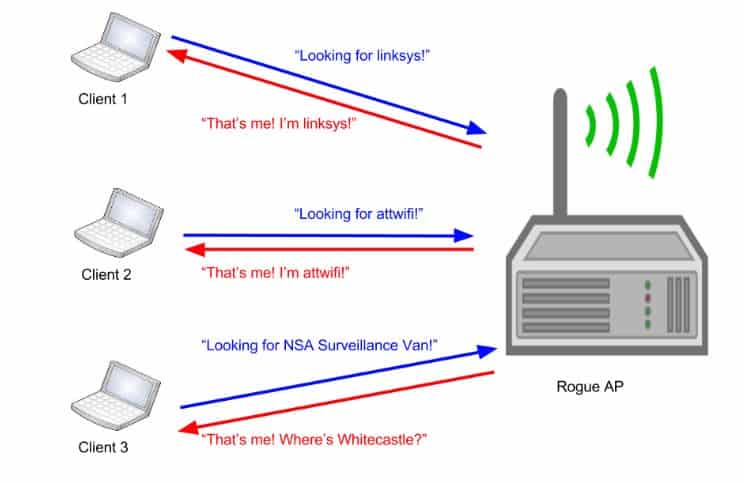
A rogue wireless device, also known as rogue access point, is a wireless access point added by a malicious attacker onto the network without authorization from the local network administrator. This will allow them to run various types of vulnerability scanners to discover the weaknesses of the system. They are used to identify and detect vulnerabilities from system misconfigurations, and flaws programming within network-based assets. These flaws can then be used to exploit the system and access all the sensitive information.
2. Peer-to-peer attacks
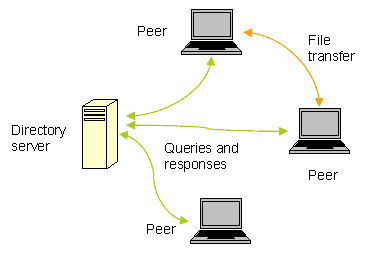
This is caused by sharing an access point with other devices. Devices that are connected with the same access point as other devices are vulnerable for this kind of wireless attacks.
To counter, most providers offer an option like “client isolation” to make sure that clients connected to the same access point can’t communicate with each other.
3. Authentication attack
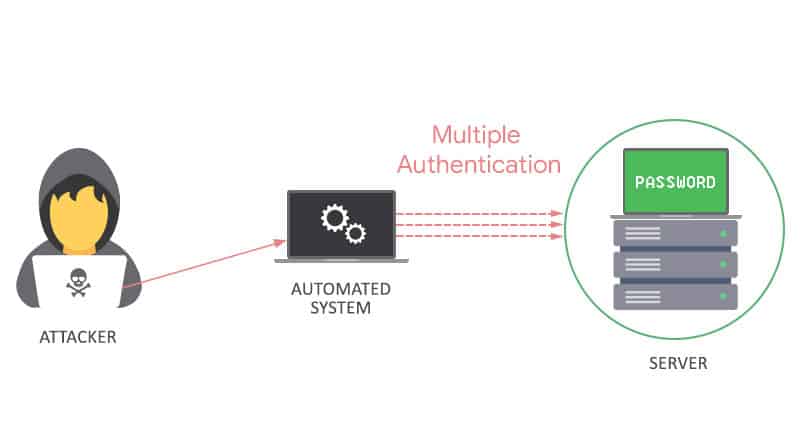
This is the most common malicious hacking most of us know. This is where an unauthorized user circumvents the security of the network system by using the vulnerability or system flaw that does not entail or contain authentication, or it does, using the login or authentication credentials. Depending on how strong the login credentials are, it only takes a few minutes for cybercriminals to gain access to the client’s account information.
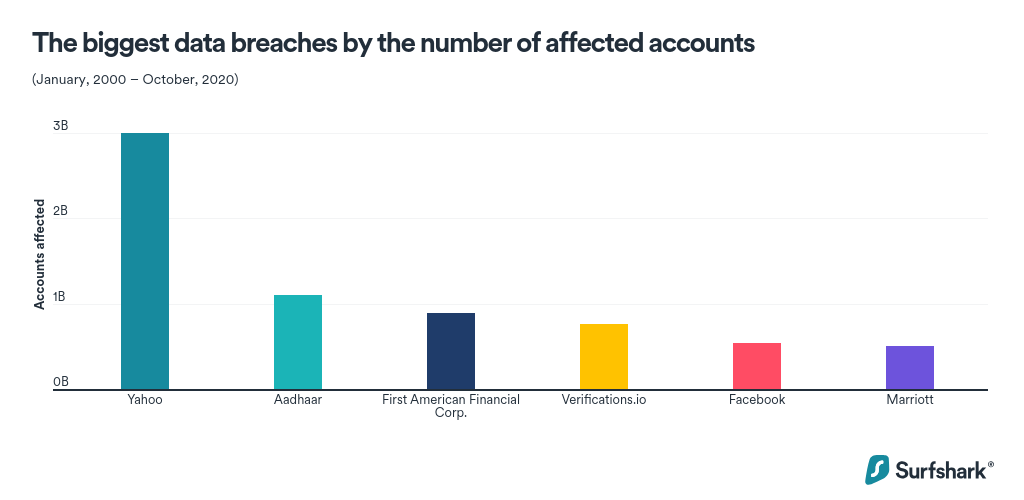
Authentication attack leads to data breach. In the year 2020 itself, there have been multiple data breaches. Below is the graph from an article on Surfshark, showing the number of accounts affected by a data breach in 2020.
4. Eavesdropping
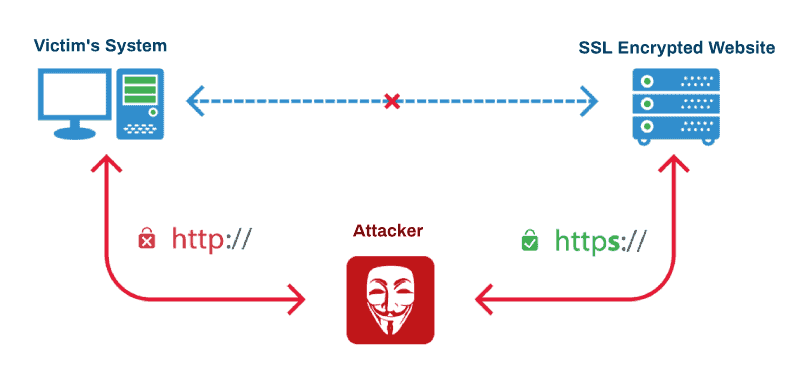
Also known as sniffing, or snooping attack is a kind of wireless network attack where wireless communication is secretly being monitored. Cybercriminals sniffs sensitive client information as it is transmitted over the network by a computer, smartphone, or any other connected devices.
There are actually two kinds of these attack. The first one is called “casual eavesdropping”, also known wardriving, where a wireless client actively scans for wireless access points. This is in no way malicious though. Software utilities like WLAN discovery actively search available WLAN networks, usually while in a moving vehicle.
The second type called “malicious eavesdropping” is the one that is illegal. This is when the cybercriminal tries to listen to the unencrypted data that is being transmitted between the client and the access point. This is why it is always essential to encrypt the network to prevent such attacks. However, it is still very possible to crack this network encryption.
Eavesdropping can be avoided with software like BitDefender which are included with some routers like Netgear R6700. Check how it works in our Netgear R6700 Review article.
5. Encryption cracking
This Wireless network attack occurs when the attacker attempts to crack the network encryption. Devices with Wired Equivalent Privacy (WEP) is the most susceptible to these attacks as it can easily be crack in less than 5 minutes (Level I Security). To prevent these attacks, you should try to use the most secure encryption available, or yet, avoid using WEP when possible.
Recommended: Top 10 Free And Paid Best Antivirus Software
6. Mac Spoofing
This happens when someone tries to change the factory-assigned Media Access Control (MAC) of a network interface on a connected device. While many businesses use MAC filtering to prevent some devices to connect to their free Wi-Fi network, some users can still bypass this MAC filtering. Some users can just spoof the MAC address of their device to the MAC address of the device that is currently registered to the network, and they’re good to go.
7. Management Interface Exploits
This is caused by using devices such as wireless controllers that will allow you to control your access point via console access or web interfaces. Since default login credentials are easily available on the internet, it is best to replace your credentials with personal, and much stronger authentication credentials.
8. Wireless Hijacking
This is when the attacker configures their laptop to broadcast access point using the same SSID as with public hotspot for example. Then unsuspecting users will unknowingly connect to this hotspot, thinking it is legit, while the attacker initiated peer-to-peer attacks, or monitor the victims’ actions on the network – such as online banking.
9. Denial of Services (DoS)
DoS attacks are when a perpetrator floods the targeted machine or resource with huge amount of requests in an attempt to overload system and prevent some or all legitimate requests from being fulfilled. Though routers like Netgear C7800 can lower the chances of DOS attack with Denial-of-service (DoS) attack protection and Double firewall protection. You can check its review on Netgear C7800 Review.
DOS attack also happens if, for example, a well less-prepared website posted a link to an article that goes on to the trend. This enormous spike in the request will lead to unintentional DoS. Just like what happened in 2009 when Michael Jackson died. Popular websites such as Twitter and Google slowed down and even crashed due to enormous number of request that is more than enough for the server to fulfill.
10. Social Engineering
This is the most common wireless attacks of all. While some of the attacks mentioned require attackers to use sophisticated script, software, or tools to initiate the attacks, social engineering does not. It can easily be done by manipulating people into giving out their information — this could either mean social media account information, or credit card information, or any other sensitive information that can be used against the client.
This can also be done by creating a fake customer service website and adding a fake phone number to manipulate unsuspecting victims to give out information or pay to things that never really exist. You can watch Jamtara on Netflix for better understanding.
How to protect your router against these attacks?
While some of the attacks is really hard to prevent, there are some that you can counter by following the tips we gathered below.
1. Don’t get a router or modem that your ISP offers
These devices are typically manufactured in bulk by companies in China and may come with some customized firmware that your ISP might not have control over. This means, security issues may take a long time to patch — sometimes it doesn’t even get any security patches at all. If you find good offers from your ISP, try to first research the company’s security track record.
2. Change default admin login credentials
Since most of the default login credentials are found online, it is best to always change the default admin login credentials. Attackers can use botnets to sniff the entire internet to look for exposed routers and try to authenticate it with the default admin login credentials, or weak and easy-to-guess passwords.
3. Secure the administrative interface
As mentioned above, some users use devices such as wireless controllers to remotely control their access point via console access or web interfaces. This will expose the admin to the internet. Since many of the vulnerabilities found in routers can also be located in their web-based management interfaces, this is not a good idea. You can set up a virtual private network (VPN) to prevent attacks with your wireless network.
4. Stop using risky services
Services that provide command-line access such as Telnet or Secure Shell (SSH) should not be exposed to the internet, or disabled even on the local network unless they’re actually needed. Researchers found that some of the backdoor accounts in routers were accessible through Telnet and Secure Shell (SSH). Since there is no way for regular users to determine whether such backdoor account exists on his router or not, it is best to just disabled such services.
5. Secure your Wi-Fi network
When setting up your Wi-Fi login credentials, choose that one that is hard to guess, or the one that only you knows about. Weird but easy to remember passphrase is more effective at making your network secure than using your widely available personal information online such as your birthday. Consider a minimum of 12 alphanumeric characters, mixed with some special symbols. Always use Wi-Fi Protected Access II (WPA2) security protocol, and do not use wired Equivalent Privacy (WEP) or Wi-Fi Protected Access (WPA) at all cost. Both are not safe, and should not be used.
You should also disable Wi-Fi Protected Setup (WPS). This feature allows devices to connect to the network using a PIN that printed on the sticker (usually at the back or at the bottom of the router). These are vulnerable to brute-force attacks. Check more about WPS in our article on What Is WPS On Router? How Does It Work?
6. Update your router’s firmware
Finally, update your router’s firmware. If your router has new firmware, it is essential that you install it first before using your network for sensitive data transmission such as mobile banking. This firmware includes patches that will fix security issues from previous OS versions. Each router has different ways of doing this, so feel free to look up online how to update your router’s firmware.