If you’re not new to the computer world, you might already know about these terms. While all of them is considered as a malware, they work differently from each other.
As we all know, malware is a short term for “malicious software”, also known as “malicious code”. It is designed to either steal information from a computer device, cause damages by inflecting codes that will destroy or corrupt files, or make your computer as a cryptocurrency miner.
Viruses, ransomware, worms, Trojan, and Bots are all different classes of malware. And today, we will try to explain each one of them, and their differences. We will also discuss other terms such as spyware, and adware.
Virus vs Worm vs Trojan vs Bot vs Spyware vs Adware
Two of the most common types of malware are viruses and worms. Both of these malicious codes has the ability to replicate themselves, or spread copies of themselves. The only difference between them is that a virus requires an active host program, or an infected active operating system to run, whilst a worm is capable to replicate and propagate itself via computer networks without any human help. We will further discuss them below.
1. Virus
As mentioned above, a virus is a type of malware that can propagate itself. However, almost all the viruses is attached to an executable file (.EXE), that means, it may exist but stay dormant in the computer and won’t be active until a user runs or open the malicious file. The infected program may function normally at early stages, but as the virus proliferates itself and infect other programs, it may start causing big problems.
A virus is capable of damaging existing data or software, or cause denial-of-service (DoS) conditions. In worst scenario, a virus can shut down your computer, or cause permanent damage to your hard drive or SSD.
A virus can be spread through P2P file transfer, network, disk, and email attachments or online downloads. It can easily be attached to a word document, or executable (.EXE) files.
2. Worm

A worm is pretty much like a virus, as both is capable of replicating, or spreading an infection. But unlike viruses, a worm doesn’t need an active host or human interaction to proliferate a functional copy of itself. A worm can infect a computer either by exploiting a vulnerability on the target computer, or use some kind of “social engineering” to trick users to execute them.
A worm can modify and delete files, and deplete system resources by making copies of itself over and over, which will slow the computer overtime. Worms can also steal data, install backdoor, and even allow cyber criminals to gain access to your personal computer.
One way to tell if your computer is infected by worms is by monitoring the hard drive space, performance, and sudden appearance of unknown files, or if you are missing any files. Perhaps, if you have files that suddenly became corrupted.
3. Trojan
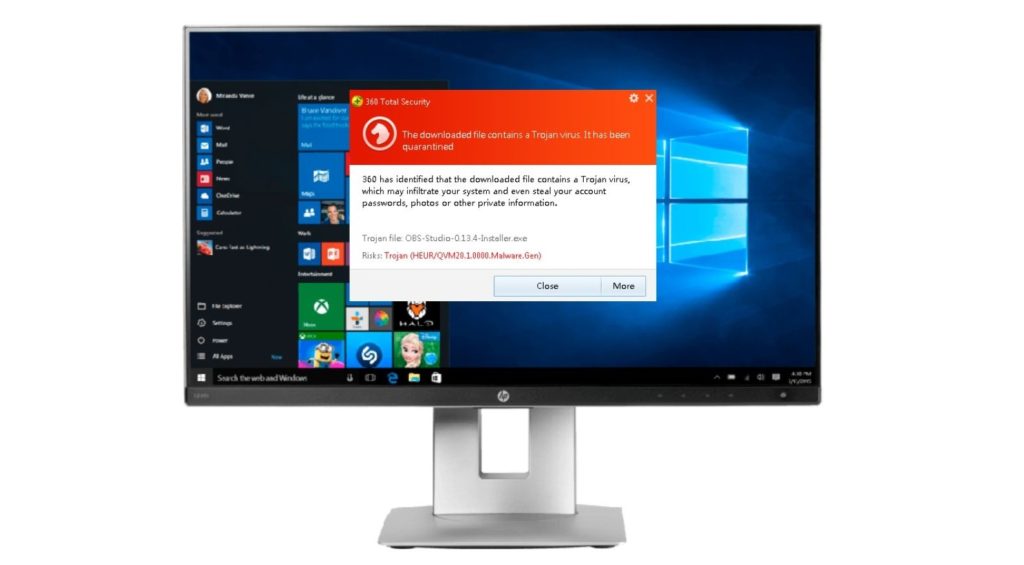
A Trojan is another type of malware which is named after the wooden horse that the Greeks used to silently infiltrate Troy. This type of malware will try to conceal its identity by making itself look legitimate. Unlike viruses and worms, Trojan can’t replicate itself.
Trojan is spread through user interactions such as opening email, or downloading and installing infected files. As it doesn’t have the ability to self-replicate, a Trojan can easily be remove by tracking the infected file, and deleting it.
While not as worst as worms and viruses, a Trojan is still capable to cause any harms. It is known to create backdoors to give hackers an easy access to your computer, deleting files, stealing data, and even activating other malware such as viruses, and adware.
4. Bot
Bot (which came from the word “robot”, also known as internet bots, spiders, crawlers, and web bots) can either be used with good or bad intentions.
Bots can be used to perform repetitive tasks such as indexing search engines, or in automatic interaction with instant messaging (in replacement of human customer service representative), but they can also be in a form of malicious code. A malicious bot can be used to gain control over someone’s computer.
Malicious bots are self-propagating malware (it has the same ability as worms for self-propagating) that infects its host, and connects back to a “command and control center” for a botnet or bot network (a network of compromised computers and similar devices).
A malicious bot can access user’s passwords, obtain financial information, log keystrokes, relay spam, launch denial-of-service (DoS) attacks, and open backdoors to an infected computer among many possible threats.
Just like other malwares, a malicious bot can infect your computer by downloading files online, or via social media or email. This can often be in a form of clickbaity photos or videos. It can also come in a form of “scare tactics” which in many times, a bot will appear telling users to install a certain software to get rid of the non-existent infection on their computer.
5. Spyware
A spyware is a type of malware that aims to access and gather user’s data without his knowledge. Like the name suggests, a spyware can also spy on all your computer activities. This information can then be used for identity theft, stealing, and even extortion.
6. Adware
An adware can either be malicious or benign. A malicious adware will bombard users with pop-up ads which ask them to click or install some bogus software with intentions of stealing data as it can also work in conjunction with a spyware.
A benign adware, on the other hand, while not malicious, can be annoying and intrusive. It will bombard users with incessant ads, to generate revenues. There are two types of revenues for adware developers, one is by displaying an ad, and the other one is on “pay-per-click” basis.
FAQs
A computer can get a virus through P2P file transfer, network, disk, and email attachments or online downloads. It can easily be attached to a word document, or executable (.EXE) files.
Boot Sector Virus – infects master boot record (encrypting the boot sector, damaging the code), and requires a full system format to remove.
Direct Action Virus – It attaches itself to an .EXE or .COM files. It will activate itself once the user executes the infected file. Aside from becoming inaccessible, a Direct Action virus doesn’t delete any file, or make a computer sluggish. It can also be easily removed using an anti-virus program.
Resident Virus – It has the ability to attach itself to an anti-virus program, and infect each files the program has scanned.
Multipartite Virus – infects both the boot sector and executable files. It will remain on the boot sector, and will immediately reproduce itself again once the user turns on the computer.
Polymorphic Virus – A Polymorphic virus has the ability to change its signature (binary pattern) every time it replicates. A file infected by polymorphic virus will look like an entirely different piece of software, eluding the detection.
A virus requires an active host program, or an infected active operating system to run, whilst a worm is capable to replicate and propagate itself via computer networks without any human interaction.
An adware can either be harmless or harmful for a computer. Adware is made to generate income by displaying intrusive ads, but it can also be used to trick users to install applications that has been infected by a malware.
Definitely. Unlike what most people believe, macOS is also vulnerable to malware just like Windows. It is just that, Windows has a higher user base, so it is a more lucrative choice for cybercriminals to target Windows users than Mac users.
However, the growing number of professionals opting for macOS to do their professional works has also attracted hackers and cybercriminals to also develop malware for macOS.